If your company offers a product or service (including cyber) that in some way could counter a potential act of terrorism, you should already know about the Department of Homeland Security’s (DHS) Support Anti-terrorism by Fostering Effective Technologies (SAFETY) Act authority. If you are familiar with the SAFETY Act, then you know that it was designed to provide liability protection in the event a plaintiff claims your product or service did not provide sufficient protection from an act of terrorism.
In the aftermath of 9/11, Congress was looking for a way to encourage the development and deployment of anti-terrorism products and services for domestic use. Some ideal candidates were available, but the fear of potential liability gave the companies that deploy these technologies pause—we do live in a particularly litigious society after all. Thus, as Sub-Title VIII to the Homeland Security Act of 2002, the SAFETY Act was born.[1]
The concept is this: if you have a product, service, standard, intellectual property, or IT offering that could be used, in some way, in whole or in part, to deter, detect, protect, or recover from a terrorist attack (e.g., on critical infrastructure), then apply to DHS for a Designation under the SAFETY Act. If the Department, via the Office of SAFETY Act Implementation (OSAI) in the Science & Technology (S&T) Directorate, concurs that the offering is effective and faces potential liability, it can statutorily limit your liability to an amount that is insurable.
In plain English, this means that if your SAFETY Act Designated “Technology” is implicated in lawsuits for supposedly not performing “well enough” during an act of terrorism (as declared at the time by DHS), you can only be held liable up to the predetermined amount set by OSAI. Further, this amount is likely covered by your insurance policies.
Importantly, the Designation that your company carries was designed in such a way that it completely immunizes your customers/users of the product or service. This is through the final regulation’s[2] language that states “There shall exist only one cause of action…only against the Seller of the Qualified Anti-Terrorism Technology and may not be brought against the…downstream users of the Technology.” This protection for your customers is likely to create valuable market differentiation.
To date, nearly 1,000 awards have been given across every threat vector related to critical infrastructure protection. Among the awards are:
- Detectors (CBRNE and Metal)
- Security Best Practices
- Life Safety Standards
- Threat and Vulnerability Assessments (Physical and cyber)
- Security Guard Services
- Specific venues (e.g., stadiums and airports) given their safety and security processes and procedures
- IT Network Appliances
- Cyber-risk SaaS
- Threat Detection Equipment Repair and Maintenance Services
- Video Surveillance and Video Management Software
- Personnel Protective Equipment
- Cargo Screening Services
- Explosive Detection Canine Teams
- Physical Security Bollards and Gates
- Mass Notification Software
In FY2016, there were 76 approved applications and as of mid-May, 57 in FY2017. FY2016 saw 144 applications submitted (a 36 percent increase over FY2015) and 84 Pre-Applications (potentially a leading indicator of future workload), a 47percent increase over FY2015. Growth continues in FY2017. Don’t read too much into the 76 to 144 ratio, this is a flowing statistic in that some applications filled in FY2015 were approved in FY 2016, as some submitted in FY 2016 were approved (or will be) in FY2017. Also, it’s not uncommon to have to refile after an application is deemed incomplete on its first submission. The average processing time for a full application is 117 calendar days (the program office has met the 120 calendar day processing efficiency metric every year since FY2008).
Further analysis of the data leads one to breakdown the nature of the offering: Is it a product or service? The distribution is about equal, with services accounting for 48 percent and products 52 percent of the total awards.
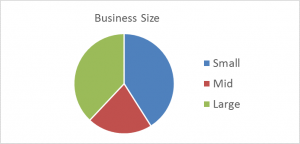
Additionally, if one looks at the size of the companies receiving protection, there is another equitable relationship as shown in the chart below. In this analysis, the business size is determined by company revenue.
OSAI reports a growing cybersecurity portfolio, some of which are given here:[3]
- February 1, 2017: Cybernance Corporation – Cybernance Platform, an enterprise-wide, web-based software tool for managing and mitigating cyber risk.
- September 20, 2016: Palo Alto Networks – Next Generation Security Platform, a family of firewall appliances.
- June 2, 2016: IBM – QRadar Security Intelligence Platform, a security information and event management (SIEM) capability.
- April 18, 2016: Acuity Solutions Corporation – BluVector cyber intelligence platform.
- March 23, 2016: Cisco Systems – Advanced Malware Protection for Networks.
- April 22, 2015: FireEye – Multi-Vector Virtual Execution Engine and Cloud Services.
Another significant critical infrastructure area with recent approvals includes providing security capabilities at commercial facilities or sports venues. This was made possible in part by the knowledge products developed from OSAI sponsored research posted on the program website.[4] For this guidance, DHS consulted with venue security directors and professionals in order to determine relevant measures of effectiveness to assess utility and feasibility of sporting and entertainment venue anti-terrorism security.
To receive the valuable benefits of SAFETY Act coverage one must apply via the DHS web site. You can begin by creating an account at SAFETYAct.gov. The application process is straightforward, however, preparing a successful application can get tricky. Essentially, you create an account, file your responses to the items in the application, and respond to follow-up questions. The items in the application ask for much information about your offering, including proof of effectiveness, evidence of reliability of the product or service, the details of the Quality Assurance policies and procedures that your offering adheres to, and details regarding the claimed potential liability that you face.
There are several details that have been left out of the discussion above, such as different “levels” of coverage. For instance, there is a special process for yet-to-be-fully-proven products and services (i.e., prototypes). This category—Developmental Test & Evaluation Designation (DTED)—is beneficial for those that want limited liability protection while deployed and collecting the appropriate data. More information can be found on the SAFETY Act web site.
In conclusion, Congress have given DHS the authority to provide your company with valuable liability protection in exchange for helping protect the public from terrorist incidents or the effects they may cause. With nearly 1,000 awards granted to date, there is equal representation between product and services and between businesses of all sizes and across all threat vectors.
[1] Pub. Law 107-296, 107th Cong. (2002) (Subtitle G of Title VIII, Homeland Security Act of 2002), https://legcounsel.house.gov/Comps/Homeland%20Security%20Act%20Of%202002.pdf.
[2] Federal Register, Vol. 71, No. 110, June 8, 2006, p. 33166, https://www.gpo.gov/fdsys/pkg/FR-2006-06-08/pdf/06-5223.pdf.
[3] Additional info under Approved Technologies at www.safetyact.gov.
[4] Best Practices in Anti-Terrorism Security (known as BPATS) for Sporting and Entertainment Venues, https://www.safetyact.gov/externalRes/refdoc/CCICADA%20BPATS.pdf.

