On September 11, 2001, we discovered that a commercial jetliner could be repurposed from a transportation device into an aerial weapon. Security efforts that had been focused on dealing with hijackers redirecting a flight to land at a different destination now had to cope with the intent not to land but to deliver a high-energy attack by crashing a plane into a ground target.
Just over 15 years later—September 20, 2016—we discovered that the interconnectivity of multiple sensors could be repurposed from a communication network into a cyber weapon. Security efforts that had been focused on protecting privacy and control over separate devices now had to cope with the intent to merge each device’s output into a massive stream of disruptive data.
Introduction
Computers do not simply compute anymore. Although what remain closest to the processing hardware are streams of digitized data, the inputs and outputs are now likely to be physical actions and reactions. Inputs coming from sensors linked to the external environment may well produce outputs that drive actuators modifying that environment.
Cyber-physical systems manipulate physical objects based on computational logic. Applications range from home appliances and medical devices to building automation, industrial machinery, and critical infrastructure components such as power, water, transportation, and emergency management. Computing failures thus affect the operation of corresponding physical systems, which can threaten safety or trigger loss of life, cause enormous economic damage, and impair vital public services.
Of course the intent is to do things better or faster, or indeed to do things not otherwise possible with earlier technologies. Yet with greater potential for positive achievement comes a greater risk of negative results. Can the expansion of benefits be adequately balanced by a corresponding expansion of control?
“The ubiquitous use of information and communication technologies has resulted in intelligent, increasingly interconnected, complex, interdependent, and therefore more vulnerable, systems. While highly dense and distributed wireless sensor-actuator networks promise a wealth of new applications and a radical improvement to the existing ones, their robustness to faults and security breaches represents a major concern.”[1]
It is the interconnectivity of cyber-physical systems that leverages and thus magnifies both their promise and threat. So-called smart devices are invested with sufficient computing power to sense, anticipate, and respond to our needs. As we manage them remotely and network them to one another we should not be surprised to encounter unexpected emergent properties.
What is the Internet of Things?
What has been styled the Internet of Things (IoT) refers to the increasing digital interconnectivity of physical objects often not initially designed as computing or communication devices. Think of it as a convergence of mobile devices, information technology networks, connected sensors, and previously isolated devices.
This digitization of society has objects and people interconnected through communication networks that report their status or that of their surroundings. Devices and machines that have not typically used internet connections are increasingly being made with some internet functions, automobiles being one of the most striking instances.
The networking of “things” (not just computing devices) actually goes back as much as 35 years, when students wishing to obtain the remote status of the soft-drink machine in the Carnegie Mellon University Computer Science Department instrumented it to become one of the first non-computer objects to go online.[2]
The International Telecommunication Union (ITU) defines IoT more grandly as “a global infrastructure for the information society, enabling advanced services by interconnecting (physical and virtual) things based on existing and evolving interoperable information and communication technologies.”[3] It further notes that “[t]hrough the exploitation of identification, data capture, processing and communication capabilities, the IoT makes full use of things to offer services to all kinds of applications, whilst ensuring that security and privacy requirements are fulfilled.”[4]
The Industrial Internet of Things (IIoT) refers to a subset of the IoT that is applied in manufacturing. This is a logical extension of automation and connectivity that has been a part of the plant environment for decades, primarily in the area known as machine-to-machine communication.[5]
One study has forecast that 6.4 billion connected things will be in use worldwide by the end of this year, up 30 percent from 2015, with some 5.5 million new things being added each day.[6] The projection is that by 2020 the total will reach 20.8 billion, half as consumer devices.
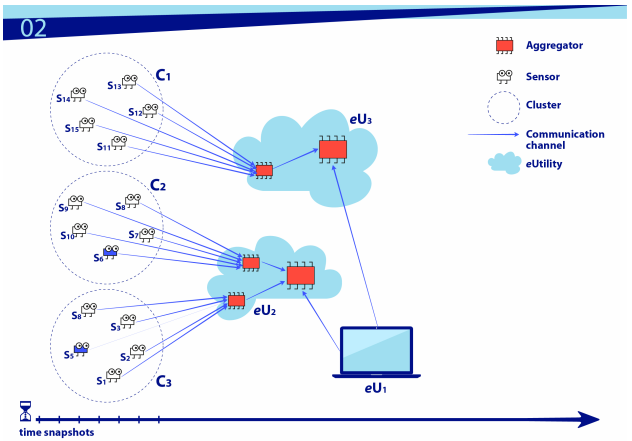
The National Institute of Standards and Technology (NIST) has recently issued NIST Special Publication 800-183, Networks of ‘Things’.[7] Its intent is to provide a framework for analyzing how the components of IoT interoperate and thus comparing security risks and reliability tradeoffs. The primitives of a Network of Things (NoT), as shown in Figure 1, are:
- Sensor,
- Aggregator,
- Communication channel,
- External utility (eUtility), and
- Decision trigger.
The report uses a data-flow model to show how the composition of primitives affects confidence in the reliability or security of a putative network. As the author explains, “[u]se case scenarios employing the primitives afford us quicker recommendations and guidance concerning a NoT’s potential trustworthiness. In short, primitives and how they can be composed create a design vocabulary for how to apply existing technologies that support IoT trustworthiness.”[8]
IoT Security Issues
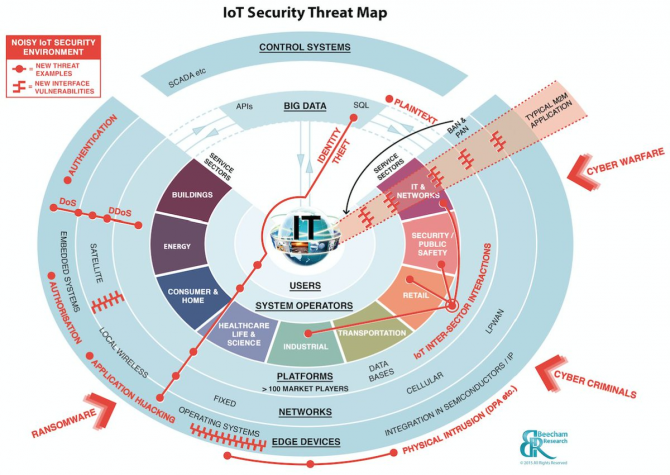
This proliferation of connected devices means that every new device brought onto the network is a new target for bad actors. IoT devices and services expand the so-called attack surface by turning physical objects that used to be offline into online assets with enhanced visibility and accessibility. Most seriously, few if any of the newly connected things were designed or originally operated with concerns about security. Embedded devices in cyber-physical systems have specialized functions and risks that are not typically addressed by traditional IT security approaches. For example, quality practitioners such as testers will have to extend their scrutiny and expertise beyond software alone to include hardware and entire systems.
The consequences of failed security span both the digital and the physical realms. Breach of a data system usually affects data: its misuse, exposure, or loss. As significant and costly as such damages might be, the damages from compromising a cyber-physical system can be much more serious, even life threatening. The power grid can fail, flights can be grounded, production lines can be shut down, machines can go out of control, and significant physical damage can occur.[10]
The increased connectivity of devices provides an expanded number of gateways for malicious access into businesses and homes. Moreover, this interconnectivity introduces novel interactions between devices, such as the exposure of automotive system to mobile apps. A wide range of new security risks and challenges emerge to the IoT devices themselves, their platforms and operating systems, their communications, and the systems to which they are connected or can communicate. Creating smarter products often removes traditional architectural barriers and offers new challenges such as impersonating “things” or denial-of-sleep attacks that drain batteries.
IoT security will be complicated by the fact that many “things” use simple processors and operating systems that may not support sophisticated security approaches. In addition, some “things” may be long-lived, allowing attackers many years to probe and discover vulnerabilities, so security responses must be flexible and able to evolve as new threats emerge during a product’s lifetime.[11]
The latest version of the Building Security in Maturity Model, built from a growing number of observations of actual software security initiatives, recognizes the growing attention to IoT security.[12] It has added IoT as a new vertical and analyzed 12 organizations (out of a total sample of 95), finding the sector less mature in general than the more established cloud, financial services, and independent software vendors verticals. Especially low-scoring practices were observed for threat modeling, architectural analysis, code review, and training.
In a recent post, security expert Bruce Schneier argued that the universe of IoT will largely remain insecure and open to compromise unless and until government steps in and fixes the problem. “When we have market failures, government is the only solution,” Schneier wrote: “The government could impose security regulations on IoT manufacturers, forcing them to make their devices secure even though their customers don’t care. They could impose liabilities on manufacturers, allowing people like Brian Krebs to sue them. Any of these would raise the cost of insecurity and give companies incentives to spend money making their devices secure.”[13]
But are there any more immediate technological means to improve IoT security?
What is Blockchain?
Imagine two individuals playing chess by mail. They agree on the initial configuration of the board in front of each of them. They exchange a sequence of moves, and they agree on the rules that determine the legality of each move. At any point, then, they will agree on the exact subsequent arrangement of pieces on the board.
Similarly, a blockchain application begins with agreement by all participants on the initial state of the system. It consists of transactions whose validity is based upon mutually acceptable rules. Consequently, there will be agreement on the state of the system at any later time.
In both cases it is not necessary for the participants to trust each other, nor do they need to appeal to any trusted external authority to arbitrate.[15]
Blockchain is typically implemented as a public database that maintains a continuously growing set of data records. It is distributed in nature, meaning that there is no master computer holding the entire chain. Rather, the participating nodes have a copy of the chain and agree on the validity of each addition to the database. The technology discourages invalid entries and ensures that the history of transactions cannot be changed.
Blockchain produces hash-chained records of transaction data, with each block linked to the previous block by including a hash of that previous block. Applying a cryptographic hash function to a file of arbitrary length generates a fixed-length string that serves as a message digest. Each block contains a hash of the previous block plus an additional transaction. It also includes a nonce, a one-time arbitrary number with time stamp, which validates the addition of the block to the chain (such as through proof-of -work or a similar mechanism). See Figure 3.
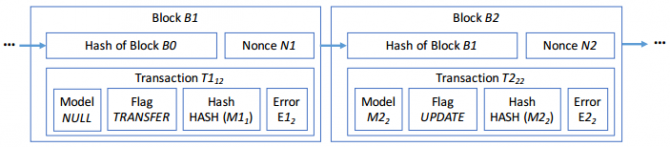
The early use of blockchain for processing and settling transactions in financial instruments was motivated by the ability to timestamp and finalize each transaction, with a mathematically proven method for confirming its validity. Although blockchain creates an immutable record that is resistant to tampering, fraud may still occur at any stage in the process but will be captured in the record and therefore easily detected.[17]
Most widely known as the ledger underpinning the bitcoin digital currency, blockchain technology can be adapted for many situations to reduce paperwork, integrating the technology into processes that include the checking of documents and identities. One compilation lists 84 potential applications ranging from mortgages to birth certificates, wills, patents, and weapons unlock codes.[18]
How can Blockchain Help Secure IoT?
The application of blockchain is proposed as a key facilitating technology to address scalability, privacy, and reliability concerns in the IoT. “Blockchain technology can be used in tracking billions of connected devices, enable the processing of transactions and coordination between devices; allow for significant savings to IoT industry manufacturers. This decentralized approach would eliminate single points of failure, creating a more resilient ecosystem for devices to run on. The cryptographic algorithms used by blockchains, would make consumer data more private.”[19]
Private industry—most prominently in banking and other financial sectors—as well as government entities worldwide are exploring blockchain. The Office of the National Coordinator for Health IT, for instance, in August 2016 announced winners of its challenge seeking industry ideas on how blockchain technology could be used in healthcare to protect, manage, and exchange electronic health information.[20]
The European Commission is planning the new IoT rules as part of a new plan to overhaul the European Union’s telecommunications laws. The Commission would encourage companies to come up with a labeling system for internet-connected devices that are approved and secure. The EU labelling system that rates appliances based on how much energy they consume could be a template for the cybersecurity ratings.[21]
The U. S. Department of Homeland Security (DHS) Science and Technology Directorate (S&T) has recently announced several awards to support the development of security solutions that involve blockchain technology: “Applicability of Blockchain Technology to Identity Management and Privacy Protection.”[22] These small competitive research grants to advance digital identity security for IoT devices were awarded through its Small Business Innovation Research program. Each business received on the order of $100,000 in preliminary funding, with potential follow-on awards:
- Digital Bazaar, Inc., Blacksburg, Virginia, is developing a Linked Data ledger format and architecture to demonstrate how to publish identity credentials.
- Respect Network Corporation, Seattle, Washington, is developing a decentralized registry and discovery service to integrate with the public blockchain.
- Narf Industries LLC, Washington, D.C., is working to achieve an identity management solution built on a permission-less blockchain: confidentiality (with selective information disclosure), integrity, availability, non-DHS repudiation, provenance, and pseudo-anonymity.
- Celerity Government Solutions, LLC, McLean, Virginia, is researching blockchain solutions to enable users to establish and maintain trusted identity transactions with public and private organizations.
DHS searches for novel ideas and technologies to improve security and situational awareness to protect the 16 critical infrastructure sectors DHS monitors. Given that the startup community has already begun to develop innovative commercial solutions for IoT, it makes sense for DHS to take advantage of this innovation.
Authenticating devices can prevent spoofing and ensure data integrity by creating an identity log that captures the identification of a device, who manufactured it, lists of available updates, known security issues and granted authorities while adding the dimension of time for added security. The goal is to limit would-be hackers’ abilities to corrupt the past records for a device, making it more difficult to spoof.
Blockchain technologies can play a major role in identity applications, as both information storage and transfer mechanisms. Trusted identity is the key to relationships—human to human, human to machine, and machine to machine—necessary in the digital ecosystem.[23]
About the Author
Taz Daughtrey (taz.daughtrey@gmail.com) is Editor of Software Quality Professional, a peer-reviewed journal published by the American Society for Quality (ASQ). Daughtrey is a Fellow of the ASQ, a Director on the American Software Testing Qualifications Board, and has taught in the Information Security master’s degree program for James Madison University.
References
[1] Norman Sadeh, “Robust, Secure, Efficient Cyber-Physical Systems,” Carnegie Mellon Univeristy CyLab, https://www.cylab.cmu.edu/research/projects/2012/robust-secure-efficient-systems.html.
[2] Stephen Ornes, “Core Concept: The Internet of Things and the Explosion of Interconnectivity,” Proceedings of the National Academy of Sciences of the United States of America 113, no. 40 (2016), http://www.pnas.org/content/113/40/11059.full.pdf.
[3] Overview of the Internet of Things, Recommendation ITU-T Y .2060 (International Telecommunications Union, 2012), http://www.itu.int/ITU-T/recommendations/rec.aspx?rec=y.2060.
[4] Ibid.
[5] Dave Turbide, “Manufacturing Embraces the Industrial Internet of Things,” IoT Agenda, http://internetofthingsagenda.techtarget.com/opinion/Manufacturing-embraces-the-Industrial-Internet-of-Things.
[6] Press Release, “Gartner Says 6.4 Billion Connected ‘Things’ Will Be in Use in 2016, Up 30 Percent from 2015” (Gartner, 2015), http://www.gartner.com/newsroom/id/3165317.
[7] Jeffrey Voas, Networks of ‘Things,’ NIST Special Publication 800-183 (2016) http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-183.pdf.
[8] Ibid.
[9] Ibid.
[10] Alan Grau, “Intrusion Detection for the IIOT: How Do We Detect Threats on the Factory Floor,” Manufacturers’ Monthly, Sept. 12, 2016, http://www.manmonthly.com.au/features/intrusion-detection-iiot-detect-threats-factory-floor/.
[11] Press Release, “Gartner Identifies the Top 10 Internet of Things Technologies for 2017 and 2018” (Gartner, 2016), http://www.gartner.com/newsroom/id/3221818.
[12] Gary McGraw, et al., Building Security in Maturity Model Version 7 (BSIMM) (2016), https://go.bsimm.com/hubfs/BSIMM/BSIMM7.pdf.
[13] “We Need to Save the Internet from the Internet of Things,” Motherboard – Vice.com, Oct. 6, 2016, https://motherboard.vice.com/read/we-need-to-save-the-internet-from-the-internet-of-things.
[14] “IoT Security Threat Map,” Beecham Research, March 5, 2015, http://www.beechamresearch.com/download.aspx?id=43.
[15] Thanks to John Kelsey, National Institute of Standards and Technology, for this analogy.
[16] Tsung –Ting Kuo, et al., ModelChain: Decentralized Privacy-Preserving Healthcare Predictive Modeling Framework on Private Blockchain Networks (HealthIT.gov), https://www.healthit.gov/sites/default/files/10-30-ucsd-dbmi-onc-blockchain-challenge.pdf.
[17] Sarah Murray, “Blockchain Can Create Financial Sector Jobs as well as Kill Them,” Financial Times, Sept. 6, 2016, https://www.ft.com/content/3a9ef8d8-33d5-11e6-bda0-04585c31b153.
[18] “Bitcoin Series 24: The Mega-Master Blockchain List,” Ledra Capital, March 11, 2014, http://ledracapital.com/blog/2014/3/11/bitcoin-series-24-the-mega-master-blockchain-list.
[19] Ahmed Banafa, “How to Secure the Internet of Things (IoT) with Blockchain,” DataFloq, https://datafloq.com/read/securing-internet-of-things-iot-with-blockchain/2228.
[20] Greg Slabodkin, “ONC Picks 15 Blockchain Ideas as Challenge Winners,” Health Data Management, Aug. 30, 2016, http://www.healthdatamanagement.com/news/onc-cites-potential-of-top-proposals-for-its-blockchain-challenge.
[21] Catherine Stupp, “Commission Plans Cybersecurity Rules for Internet-Connected Machines,” EurActiv.com, Oct. 5, 2016, https://www.euractiv.com/section/innovation-industry/news/commission-plans-cybersecurity-rules-for-internet-connected-machines/.
[22] “News Release: DHS S&T Awards $1.3 Million to Small Businesses for Cyber Security Research and Development,” U.S. Department of Homeland Security, Aug. 12, 2016, https://www.dhs.gov/science-and-technology/news/2016/08/12/news-release-dhs-st-awards-13-million-small-businesses-cyber.
[23] Irving Wladawsky-Berger, “Digital Identity: Key to Privacy, Security in a Modern Economy,” The Wall Street Journal, Sept. 2, 2016, http://blogs.wsj.com/cio/2016/09/02/digital-identity-key-to-privacy-security-in-a-modern-economy/?mod=djemCIO.
[24] Zach Wilkholm, “When Vulnerabilities Travel Downstream,” Flashpoint, Oct. 7, 2016, https://www.flashpoint-intel.com/when-vulnerabilities-travel-downstream/.
[25] Lorenzo Franceschi-Bicchieri, “How 1.5 Million Connected Cameras Were Hijacked to Make an Unprecedented Botnet,” Motherboard – Vice.com, https://motherboard.vice.com/read/15-million-connected-cameras-ddos-botnet-brian-krebs.
[26] Brian Krebs, “Source Code for IoT Botnet ‘Mirai’ Revealed,” Krebs on Security, https://krebsonsecurity.com/2016/10/source-code-for-iot-botnet-mirai-released/.
[27] Lorenzo Franceschi-Bicchieri, “The Internet of Things Sucks So Bad Even ‘Amateurish’ Malware is Enough,” Motherboard – Vice.com, http://motherboard.vice.com/read/internet-of-things-malware-mirai-ddos.
[28] “The Internet of Stings,” The Economist, Oct. 8, 2016, http://www.economist.com/news/science-and-technology/21708220-electronic-tsunami-crashes-down-solitary-journalist-internet.

