Nate Evans, Frédéric Petit, and Amanda Joyce, Risk and Infrastructure Science Center
Global Security Sciences Division, Argonne National Laboratory
Introduction
In February 2013, Executive Order 13636, Improving Critical Infrastructure Cybersecurity, emphasized the need to develop and implement a flexible cybersecurity framework, consistent with existing standards, to identify, assess, and manage cyber risk.[1] In February 2014, the National Institute of Standards and Technology (NIST) issued the Framework for Improving Critical Infrastructure Cybersecurity, which defines five core functions for improving the protection and resilience of critical infrastructure: identification, protection, detection, response, and recovery.[2] This framework identifies the importance of cyber dependencies within the protection and resilience assessments of critical cyber services. Several other policy documents—including Presidential Policy Directive 21: Critical Infrastructure Security and Resilience,[3] the 2013 National Infrastructure Protection Plan,[4] and the Voluntary Private Sector Preparedness Program[5]—highlight the importance of considering both physical and cyber dependencies in protection and resilience assessments. This paper presents an overview of elements characterizing cyber dependencies and how they have been included in an assessment tool developed by Argonne National Laboratory for the Department of Homeland Security (DHS) Office of Cybersecurity and Communications.
General Definitions
Several taxonomies have defined the notions of cyber or informational dependencies. Table 1 presents some of these definitions.
Table 1 – Definitions of Cyber Dependencies
| Taxonomy | Name | Definitions | |
| Rinaldi, Peerenboom, and Kelly – 2001[6] | Cyber | An infrastructure has a cyber dependency if its state depends on information transmitted through the information infrastructure. | |
| Pederson et al. – 2006[7] | Informational | An informational or control requirement between components. For example: a supervisory control and data acquisition (SCADA) system that monitors and controls elements on the electrical power grid. A loss of the SCADA system will not by itself shut down the grid, but the ability to remotely monitor and operate the breakers will be lost. | |
| Clemente – 2013[8] | Informational | An informational or control requirement between components. | |
A cyber dependency can therefore be defined as an informational or data linkage or connection between two assets, by which the state of one asset influences or is reliant upon the state of the other. An asset has a cyber dependency if its operation depends on information transmitted via electronic or informational links (Figure 1).
Transfer and processing of cyber resources (e.g., data, information) are principally done by two critical infrastructure sectors: Communications (transmission of data and information) and Information Technology (use and processing of data).
In general, Cyber Security seeks to protect computer systems from intrusions and acts of malice. This concept is very important in the context of business continuity; however, other elements must be considered when assessing the resilience of cyber systems and when addressing cyber dependencies. It is also important to consider how quality of service (QoS) and network performance (NP) can affect the functions of a given critical cyber service (CCS). QoS represents the degree of satisfaction of the service user and NP represents the ability of a communication network to provide the functions related to the exchange of data between users. The QoS is representative of the service agreement between the user and the provider and characterizes the degradation of a CCS in relation to the possible degradation of data. Several standards define the parameters (e.g., transfer rate, latency, speed, and data accuracy) that can be used for characterizing the QoS.[10]
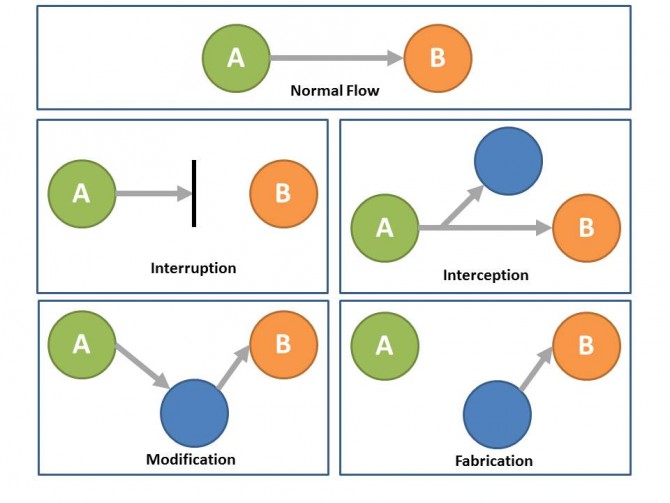
NP, which is the ability of a network to provide the functions related to communications among users, directly affects the QoS, as the degradation of the data transfer mode will necessarily result in a deterioration of the data and thereby the degree of user satisfaction. The degree of user satisfaction can be qualified in terms of acceptable level of consequences. In the context of CCS, degraded user satisfaction may mean cyber but also physical consequences. NP can be characterized according to the quality of data flow. Figure 2 shows how the data flow may be affected by different threats and therefore cause the degradation of the data quality.
During normal operations, a normal flow of data exists between the provider asset (or transmitter) and the user asset (or receiver). Several threats may occur:
- Flow interruption, when the data do not go to the receiver. The interruption thus affects data availability.
- Flow interception, when the data are captured between the transmitter and the receiver. The interception thus affects data confidentiality.
- Flow modification, when the data are processed (degraded) before reaching the receiver. The modification thus affects data integrity.
- Flow fabrication, when the data received by the receiver are not originating from the good transmitter. The fabrication thus affects data authenticity.
When assessing cyber dependencies, it is therefore important to consider the QoS, NP, and security threat but also to characterize the operating environment, coupling and response behavior, type of failure infrastructure characteristics, and state of operations as presented in Petit et al.[12]
Use in the Cyber Protection Resilience Index (CPRI)
Argonne’s Global Security Sciences (GSS) Division’s Risk and Infrastructure Science Center has developed a composite measure, the CPRI, which is intended to serve as an indicator of the effectiveness of an organization’s cyber protection and resilience programs as it relates to a CCS and to allow organizations to compare cybersecurity information with that of similar organizations within the sector. The approach takes into account the diverse nature of cyber protection and resilience programs and uses the principles of Multi-Attribute Utility Theory[13] to aggregate five main attributes characterizing the effectiveness of an organization’s cyber protection and resilience program in a single index:
- Cybersecurity Management;
- Cybersecurity Forces;
- Cybersecurity Controls;
- Incident Responses; and
- Dependencies.
The methodology considers the relative importance of each element constituting the organization’s cyber protection and resilience program for the overall protection and resilience of the CCS by attributing a specific weight to each element. The CPRI therefore varies from 0 (low protection and resilience) to 100 (high protection and resilience). This method for characterizing the resilience of a critical infrastructure makes it possible to consider the specificity of all critical infrastructure subsectors and to compare the efficiency of different measures in enhancing protection and resilience in the studied system. The CPRI for each alternative or program studied can then provide guidance to a decision maker on the relative effectiveness of each alternative for achieving the intended objective and can be compared across a set of like cyber services and similar facilities and serve as a guide for supporting decision making.
In the CPRI, dependencies refer to the transfer and processing of data and are subdivided into four subcomponents:
- Data at Rest;
- Data in Motion;
- Data in Process; and
- End Point Services.
The three first subcomponents represent the three possible states of data. Data at rest characterizes data being physically stored, including storage capabilities and specificities. Data in motion characterizes data as they are in transit, including the processes and equipment (e.g., switches, networks, and firewalls) used for the transfer of data. Data in process (or data in use) characterizes data under change, including mainframes and clusters. The fourth and last category, end point services, characterizes computer hardware devices (e.g., desktops, laptops, tablets) and their specificities.
Each type of cyber dependency is characterized in terms of needs, impacts, and resilience management measures. Table 2 presents the general components considered in the CPRI.
Table 2 – Cyber Dependency Components Considered in the CPRI
| Components | Characteristic |
| Needs |
|
| Impacts |
|
| Resilience Measures |
|
Unlike other types of cyber dependencies, data in motion differentiates between internal and external communication. The components used for identifying the cyber dependencies allow incorporating the influence of existing relationships with other CCSs on the protection and resilience of the critical infrastructure’s CCS. The percentage of normal cyber functions lost or degraded is a proxy variable that includes the consideration of existing protective measures. The resilience measures are addressed with the consideration of the existence of business and contingency planning. The definition of impact also allows integration of QoS requirements.
The CPRI also allows assessing the degradation of NP by discriminating between five types of threats:
- General threat or hazard;
- Distributed Denial of Service;
- Natural Disaster;
- Remote Malware (confidentiality); and
- Destructive Malware (integrity).
Future Developments
More research and development are needed to fully understand and identify the effect of cyber dependencies and interdependencies on the protection and resilience of a CCS and ultimately the protection and resilience of critical infrastructure. Assessment of cyber dependencies should be refined by identifying and integrating the CCS requirements in terms of QoS and NP. All critical infrastructure interactions (i.e., upstream, internal, and downstream) and dimensions influencing critical dependencies (i.e., operating environment, coupling and response behavior, type of failure, infrastructure specificities, and state of operation) must be considered to operationalize dependency and interdependency analysis in risk and resilience assessment. Analysis capabilities should also evolve towards an integration of methodologies and tools and a better integration and comprehension of cyber and physical dependencies.
The CPRI is still in its early stages of use within the DHS cyber community. The index will be regularly reviewed and enhanced to integrate specific stakeholders’ requirements. Among other enhancements, additional threat scenarios could be developed for better integrating QoS and NP elements.
Conclusion
Considering and understanding cyber dependencies are important for enhancing the protection and resilience of critical infrastructure and complex systems. Cyber dependencies are complex elements to identify and analyze. Even if more work is required to fully comprehend the criteria influencing the cyber relationships among critical infrastructure systems and their importance for the security and resilience of these complex systems, the CPRI proposes an innovative approach for integrating cyber dependency considerations into the evaluation of the protection and resilience of critical cyber system.
Acknowledgments
The submitted manuscript has been created by UChicago Argonne, LLC, Operator of Argonne National Laboratory (“Argonne”). Argonne, a U.S. Department of Energy Office of Science laboratory, is operated under Contract No. DE-AC02-06CH11357. The U.S. Government retains for itself, and others acting on its behalf, a paid-up nonexclusive, irrevocable worldwide license in said article to reproduce, prepare derivative works, distribute copies to the public, and perform publicly and display publicly, by or on behalf of the Government. The development of the tools presented in this paper has been funded by the U.S. Department of Homeland Security Office of Cybersecurity and Communications under Contract No HSHXDC-13-X-00223. If you would like more information regarding the information presented in this paper, please contact Nate Evans at nevans@anl.gov.
[1] Executive Order 13636: Improving Critical Infrastructure Cybersecurity, 78 Fed. Reg. 11739 (Feb. 19, 2013), available at http://www.gpo.gov/fdsys/pkg/FR-2013-02-19/pdf/2013-03915.pdf.
[2] National Institute of Standard and Technology, “Framework for Improving Critical Infrastructure Cybersecurity,” February 12, 2014, http://www.nist.gov/cyberframework/upload/cybersecurity-framework-021214.pdf.
[3] White House, Presidential Policy Directive PPD 21—Critical Infrastructure Security and Resilience, Feb. 12, 2013, available at https://www.whitehouse.gov/the-press-office/2013/02/12/presidential-policy-directive-critical-infrastructure-security-and-resil.
[4] NIPP 2013—Partnering for Critical Infrastructure Security and Resilience (Washington, DC; U.S. Department of Homeland Security, 2013), available at http://www.dhs.gov/sites/default/files/publications/NIPP%202013_Partnering%20for%20Critical%20Infrastructure%20Security%20and%20Resilience_508_0.pdf.
[5] The Voluntary Private Sector Preparedness Program—PS-Prep™ & Small Business Preparedness, Federal Emergency Management Agency, updated Oct. 6, 2015, available at http://www.fema.gov/voluntary-private-sector-preparedness-program-ps-preptm-small-business-preparedness.
[6] Steven M. Rinaldi, James P. Peerenboom, and Terrence K. Kelly, Identifying, Understanding, and Analyzing Critical Infrastructure Interdependencies, IEEE Control Systems Magazine, Dec. 2001, available at http://user.it.uu.se/~bc/Art.pdf.
[7] P. Pederson, D. Dudenhoeffer, S. Hartley, and M. Permann, Critical Infrastructure Interdependency Modeling: A Survey of U.S. and International Research, Idaho National Laboratory, Aug. 2006, available at http://cip.management.dal.ca/publications/Critical%20Infrastructure%20Interdependency%20Modeling.pdf.
[8] Dave Clemente, Cyber Security and Global Interdependence: What is Critical? (London; Chatham House, 2013, available at https://www.chathamhouse.org/sites/files/chathamhouse/public/Research/International%20Security/0213pr_cyber.pdf.
[9] F. Petit, D. Verner, D. Brannegan, W. Buehring, D. Dickinson, K. Guziel, R. Haffenden, J. Phillips, and J. Peerenboom, Analysis of Critical Infrastructure Dependencies and Interdependencies, (Argonne, Ill.; Argonne National Laboratory, Global Security Sciences Division, 2015) ANL/GSS-15/4.
[10] International Communication Union, Quality of Service and Network Performance Handbook, ITU-T Telecommunication Standardization of ITU(Geneva; ITU, 2004).
[11] Ibid.
[12] Petit et al., Analysis of Critical Infrastructure Dependencies.
[13] Ralph Keeney and Howard Raiffa, Decision Analysis with Multiple Objectives: Preferences and Value Tradeoffs (New York; Wiley and Sons, Inc., 1976).