This article consists of several excerpts from the author’s upcoming NANOKRIEG: BEYOND BLITZKRIEG, a book on redefining and re-arranging the Military Infrastructure, Natural Destructive Strategies, Energy, & Tactics (MINDSET) needed to fight the War on Terrorism.
Today’s terrorist attacks are sometimes totally unforeseen and unanticipated. Our intelligence cannot be one or two steps behind. Our response has to be quick and decisive.
The Platform for War needed to provide a resilient decision framework for forces to meet and defeat hostilities within a 21st-century global environment has seven important phases of conflict:
- Monitoring (the Enemy/Threat),
- Measuring (the Threat/Intensity),
- Making the Decision to Respond,
- Mobility of Forces and Resources,
- Management of the Conflict/ Sustaining the initiative,
- Making sure the conflict is over and peace is re-instated to the region, and
- Maintaining a presence (if necessary)
When looking at these seven phases, we must ask ourselves, “have we done a good job and learned any lessons in previous wars and conflicts to maximize our intelligence, our efforts, and applied resources in each one of these phases?” (See CHART 1)
The seventh phase, “Maintaining a presence” needs to be decided upon and not automatically left out. You can’t win the war and then walk away prematurely. Iraq is a good example where the strategy expended all the resources in winning the war with no afterthought to maintaining a presence to insure a full recovery to normalcy. We cannot omit this critical step.
Infrastructure must be able to sustain unpredicted attack scenarios. Software-based systems must be resilient and attack-tolerant. The Five Rs of Mission Critical systems should be adhered to in all important intelligent infrastructure: Reliability, Redundancy, Robustness, Resiliency and Resistance-to-attacks.
CHART 1: PLATFORM FOR WAR: Seven Phases of Conflict
| PHASE | ACTION | DESCRIPTION |
| 1 | MONITORING THE ENEMY | Any organized group bent on terror should be under constant surveillance. |
| 2 | MEASURING THE THREAT | The strength of both their internal & external resources, trained forces, and ability to strike should be measured and assessed. |
| 3 | MAKING THE DECISION TO RESPOND | As soon as the threat level is determined to be real and dangerous, a decision to respond is made. |
| 4 | MOBILITY OF FORCES & RESOURCES | To counter the threat, the right amount of resources and support is assigned. |
| 5 | MANAGEMENT OF THE CONFLICT | Oversight and ongoing management of all actions and counter-actions are required. |
| 6 | MAKING SURE THE CONFLICT IS OVER | After the threat is eliminated, the situation goes back to normal. |
| 7 | MAINTAINING A PRESENCE (if necessary) | If deemed necessary, a maintenance force is kept in place to keep any future insurrection neutralized. |
Source: Upcoming book, James Carlini, Nanokrieg Beyond Blitzkrieg,
GOING BEYOND BLITZKRIEG
If we go back to the 1930s, the Germans were far ahead in their thought process for new weapons and tactics compared to other Europeans countries and the United States. Science and new weaponry built with new technologies were considered, “the fast lane to world domination.”
The Germans raised the bar substantially between World War I and World War II undertaking new strategic directions as well as refining established ones. Blitzkrieg was only one strategy (combining Air and Land strategies in a fast-paced attack). Their U-Boat Strategy was also strategically refined and continued from World War I to control major regions in the Atlantic Ocean.
What they lacked was an aircraft carrier. (And in many ways, that was their demise at sea). Battleships were more of a World War I technology, but carriers were the right platform of war at sea to deliver the fight past the horizon in World War II.
There was also the strategy of developing “Wonder Weapons” (Wunderwaffen), like guided ballistic missiles, the Nazi Bell (Die Glocke), and others which they initiated. Not a lot of information survived on the advanced research of “Die Glocke”, the magnetic-based (anti-gravity), propulsion weapons system. The Nazis allegedly shot almost everyone affiliated with the project, so the Allies would not get all the development concepts, detailed blueprints, and research results of the technology. Others say they shipped many parts of the research and technology to a base in South America or Antarctica to be worked on down there.
In doing research on the Nazi Bell, it is clearly evident Nazi scientists working on this technology platform took a radical departure from traditional propulsion development approaches commonly used for other conventional weapons. Their research into anti-gravity or magnetic-based propulsion was a giant step into a strategic direction of a whole new area that other world scientists were not as immersed in and/or committed to. Anything confiscated on this subject at the end of the war was quickly stamped, “Top Secret” and “Classified”.
The introduction of jet fighters in combat is attributed to the Nazis. The ME-262 was a real, working fighter, not just an unfunded prototype on a British drawing board.
The Nazis were far ahead of everyone in proto-typing and developing “wonder-weapons” and new military infrastructure. We were lucky we defeated them before they had a chance to mass-produce prototypes and use their new weapons, like jet fighters, effectively.
Their whole focus on sophisticated rocketry (guided missiles) was probably 20-30 years ahead of everyone else. Most of the rocket scientists, along with several thousand other Nazi scientists, were relocated from Germany into the United States working on rocket systems and other military weaponry systems to medicine to sound wave technologies.
POST-WAR
Coming out of World War II, the U.S. gained momentum from an economic standpoint on most countries due to the fact American factories were not blown apart during the war. But as time went on, this meant we did not have to rebuild and upgrade factories, leading to the demise of United States manufacturing.
Since World War II, the speed of war and decision to apply resources for response has accelerated. What used to take days or months to mount an offensive can be done in a matter of seconds depending on the technology platform used. Countermeasures need to be responsive in less than seconds.
If we apply the same speeds of transaction processing of HFT (High Frequency Transaction) servers used in the stock market to offensive and defensive weapons, the response to a major attack could be as little as a couple of microseconds. Hence, the new label of military strategy, NANOKRIEG©. The window of time for attack and counter-attacks has shrunk and right decisions must be made accordingly.
With the incident that happened at the NYSE on July 8th, 2015, closer monitoring of their network should be required. Mission critical networks should not go down for hours if the proper redundancy has been engineered into the application. What unknown vulnerability was uncovered in that event? The whole story was not told. Could that same type of failure be initiated by an external cyber-terrorist?
WHAT HAPPENS WHEN PLAYBOOKS BECOME OBSOLETE?
The military and related U.S. Government agencies, like the U.S. Department of Homeland Security and the NSA (National Security Administration), have created various exercises and war simulations designed to offer training to respond to various offensives. Unfortunately, they have sometimes missed the mark when it comes to actually being prepared and able to respond to real threats. 9/11 (2001) was a great example of not being prepared or having that type of scenario to respond to in their playbook for security and national defense.
The problem might be everyone is thinking along the same lines and no one is thinking outside the “traditional threats and attacks” which they have studied and prepared for multiple times. This is not a new observation.
General George S. Patton pointed this out years ago when he said, “If everyone is thinking alike, then someone isn’t thinking.”
The Framework for MINDSET is divided into an equivalent Defensive and Offensive layered structure of Warfare and Weapons, their effective ranges and coverage. (See CHART 2)
Traditional weapons would include everything we have used since World War II. Planes, ships, tanks, helicopters, artillery, small arms, and all conventional weapons would be defined in this layer of weapons. (Also included, the Atomic weapons layer, since they were used in World War II.)
The Drone layer would include all the types of drones currently in use and in addition, any new generation of drones being developed. (A wrist-based drone is already being developed.)
Bio weapons would include anything spread through biological means.
Entomological weapons would include anything spread by insects, including some form of biological (natural or synthetic) virus/disease. The insect becomes the carrier of the weapon. (Too far-fetched? A natural delivery system (using mosquitos) was tested successfully back in 1955.)
Seismic weapons would include anything used to create a seismic disorder to create natural disasters (earthquakes or tidal waves).
Weather weapons could create droughts or major storms. (Some tactics include Cloud seeding, ChemTrails, but this is an area not overly discussed.)
Soundwave technology would use amplified sound waves to incapacitate personnel, crowds, or create natural disasters.
Lightwave/lasers could be used in many applications both on earth and in space.
DIAGRAM 1: EFFECTIVE RANGE FOR EMP
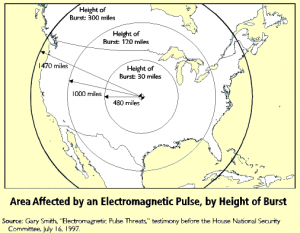
EMP (Electro-Magnetic Pulse) bombs were a concern in the Cold War but then, fell off the radar after it ended. They have become a more current threat based on the ability of a terrorist organization to build something like this and not have to build a very sophisticated delivery system for it. (See DIAGRAM 1)
Cyber weapons would include those on the Internet, Social Media, and Smartphones. Social media is already in use as a successful recruiting tool for terrorist organizations like ISIS.
Space weapons are not fantasy or far into the future anymore. The SDI (Strategic Defense Initiative) weapon system was proposed decades ago by Ronald Reagan. Offensive systems like Psychotropic weapons have been discussed and documented by other military strategists.
CHART 2: FRAMEWORK FOR MINDSET (MILITARY INFRASTRUCTURE, NATURAL DESTRUCTIVE STRATEGIES, ENERGY, & TACTICS – DEFENSE)
| TYPE OF WARFARE & WEAPONS | EFFECTIVE COVERAGE AREA | DEFENSES |
| Traditional | Local, Regional, Continental and Intercontinental | * |
| Atomic | Intercontinental | * |
| Drone | Local, Regional | * |
| Bio | Regional, Continental, Intercontinental | * |
| Entomological (Insects) (Potential delivery system for Bio) |
Local, Regional, Continental | * |
| Seismic (Tectonic) | Regional, Continental, Intercontinental | * |
| Weather | Local, Regional, Continental | * |
| Soundwave (Audio) | Local (Future Regional?) | * |
| Lightwave (Laser) | Local, (Line-of-sight) | * |
| EMP (Electro-Magnetic Pulse) |
Regional, Continental and Intercontinental | * |
| CYBER (Internet & Smartphones) |
Global through the Internet Infrastructure | * |
| Space | Planetary & Interplanetary | * |
Source: James Carlini
* Not disclosed
REFINING THE MINDSET FRAMEWORK
Types of measures and counter-measures for each layer will be discussed in detail in the book. We cannot apply traditional weapons and approaches for future conflicts.
Big Data is also a large area of interest. The equivalent of Big Data (civilian side) is a domestic surveillance system on the military side providing “Total Information Awareness” (TIA) as it relates to cellphone conversations, e-mail discussions, and credit information like banking, spending patterns, and social network interactions from family to business connections. With that type of detail-rich data base, many connections and interrelationships of data will be available to review, assess, and analyze.
If we apply a traditional strategic focus in future conflicts, we will wind up like the Polish Cavalry facing the approaching Blitzkrieg tanks and dive bombers of the German Army in World War II. Bringing old technology, outdated strategies, and last century’s tactics into the NANOKRIEG© battlefield will guarantee a short, one-sided battle and a quick surrender, if not total annihilation.
About the Author
James Carlini, MBA, is a strategist for mission critical networks, technology, intelligent infrastructure, and President of Carlini & Associates, since 1986. Author of LOCATION LOCATION CONNECTIVITY, Next-Generation Real Estate, Intelligent Infrastructure, Technology, and the global Platform for Commerce (Published 2014).
A former award-winning adjunct faculty member at Northwestern University in both the Executive Masters and undergraduate programs (1986-2006) developing and teaching courses in technology management, team dynamics, Six Sigma, Network Security, and international applications of technology.
His original “Platform for Commerce” definition of infrastructure and its impact on economic growth is referred to in the US ARMY Corps of Engineers’ Handbook, “Infrastructure and the Operational Art” (2014)

